Introduction: Security as “Job Zero”
At DigitalCloudAdvisor (DCA), we firmly believe that in today’s digital world, security is not an afterthought---it’s “Job Zero”, just as AWS advocates.
From servers to applications, user permissions to sensitive datasets, we embed security best practices across every layer of the AWS environment. One critical pillar in our cloud security strategy is AWS Key Management Service (KMS) --- a powerful managed service that simplifies encryption and protects critical data assets.
In this blog, we’ll guide you through how AWS KMS works, why it matters, and how DigitalCloudAdvisor helps companies like yours design resilient, compliant, and scalable encryption architectures.
Understanding AWS KMS: More Than Just Encryption
AWS Key Management Service (KMS) provides centralized control over cryptographic keys and enables secure encryption of data across AWS services.
Built with FIPS 140-2 validated Hardware Security Modules (HSMs), AWS KMS not only manages encryption keys but also integrates natively with services like Amazon S3, EBS, RDS, Redshift, and Lambda.
By using KMS, businesses can:
- Encrypt sensitive workloads easily
- Meet compliance frameworks (GDPR, HIPAA, PCI-DSS, ISO 27001)
- Reduce operational complexity and human error
Types of Keys in AWS KMS
KMS offers three types of keys, giving you flexibility based on your control needs:
Customer-Managed Keys - Created and controlled entirely by you. Full flexibility over permissions, policies, rotation, and audits.
AWS-Managed Keys - Created automatically by AWS services (e.g., for encrypting EBS volumes or RDS databases). Visible but managed by AWS.
AWS-Owned Keys - Fully abstracted keys owned by AWS, used for backend encryption of service resources. No customer visibility or management.
At DCA, we often recommend Customer-Managed Keys for critical assets to ensure full control, compliance, and visibility.
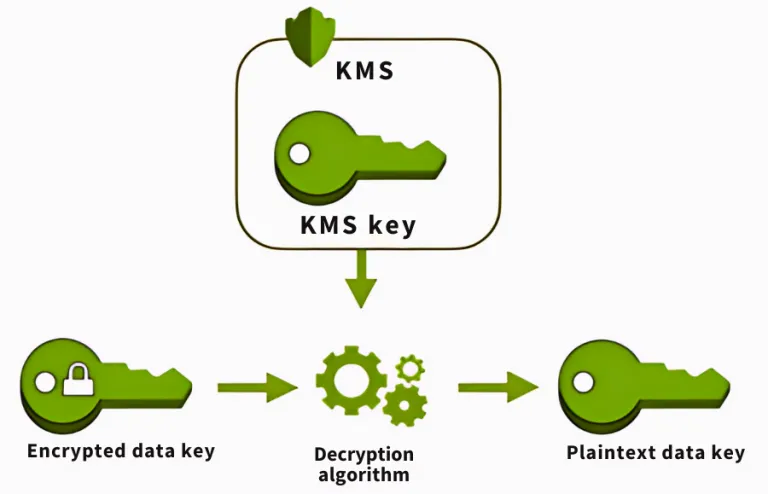
Key Concepts: Encryption, DEKs, and Quotas
KMS Keys (CMKs):
- Core resource representing the cryptographic key material.
- Metadata includes key ID, usage type, state, policy, and creation timestamp.
- The key material never leaves AWS KMS unencrypted.
Data Encryption Keys (DEKs):
- Used to encrypt large volumes of data outside KMS.
- Can be generated and stored securely alongside the encrypted data.
- Decrypted temporarily via KMS for actual encryption/decryption operations.
🔒 Important Quotas to Know:
- 100,000 KMS keys per account (adjustable)
- 50 aliases per key
- 32 KB Key policy document size
- 50,000 grants per key (adjustable)
Symmetric vs Asymmetric Encryption
- Symmetric Encryption: Same key for encrypting and decrypting data. Faster, ideal for large data volumes.
- Asymmetric Encryption: Public/private key pairs. Used for secure key exchanges, digital signatures, and compliance-driven use cases.
Whether symmetric or asymmetric is better depends on your specific business requirements and regulatory needs.
At DCA, we guide our customers on selecting the right method based on security risk assessments and operational goals.
The Importance of Key Rotation and Lifecycle Management
Key rotation strengthens security by reducing the window of key compromise.
AWS KMS offers:
- Automatic key rotation (yearly) for Customer-Managed Keys
- Manual rotation options for more frequent updates
- Tools to archive old keys securely
⚡ Pro Tip from DCA: Set up CloudTrail logging to audit every use of your encryption keys and detect anomalies early.
Potential Risks: Planning for Key Loss or Disablement
What happens if a key is accidentally disabled, scheduled for deletion, or becomes compromised?
Without a proper recovery plan, you risk losing access to encrypted data permanently.
DCA always recommends:
- Implementing strict IAM policies to limit key management permissions
- Using key deletion protection
- Enabling CloudTrail monitoring and alerts
- Developing and testing a Key Recovery and Disaster Recovery Plan regularly
Integrations: Extending AWS KMS Across Your Environment
AWS KMS integrates deeply across services like:
- Amazon S3 (bucket and object encryption)
- Amazon EBS (volume encryption)
- Amazon RDS (database storage encryption)
- AWS Secrets Manager (secret encryption)
- AWS Lambda (environment variable protection)
You can also create Private VPC Endpoints (via AWS PrivateLink) to AWS KMS, ensuring all encryption operations happen securely inside your network boundary.
Access Control: Using Key Policies, IAM, and Grants
Controlling access to encryption keys is crucial:
- Key Policies: Attached directly to the KMS key. Primary access control layer.
- IAM Policies: Allow cross-service or role-based key usage.
- Grants: Temporary permissions for specific AWS services or users.
- VPC Endpoint Policies: Fine-grained control over who can call KMS APIs inside your VPC.
✅ DCA Tip: Always follow the principle of least privilege when granting access to your encryption keys.
Why Trust DigitalCloudAdvisor with Your AWS Encryption Strategy?
At DigitalCloudAdvisor, we combine technical excellence with a business-first approach to cloud security. When it comes to AWS KMS and encryption:
- We design encryption architectures tailored to your industry’s compliance needs.
- We implement key lifecycle automation for minimal operational burden.
- We build proactive monitoring and alerting into your environment.
- We help you achieve full regulatory alignment without compromising on scalability or agility.
Security is not a checkbox---it’s a continuous journey, and we walk that path with you.
Conclusion: Secure Your Future with DCA and AWS KMS
Encryption is your last line of defense.
Whether you’re protecting customer data, intellectual property, or critical business assets, AWS KMS provides the robust encryption foundation you need --- and DigitalCloudAdvisor ensures it’s designed, implemented, and maintained for maximum security and operational excellence.




